How to Detect Ransomware With FileAudit
What Happens When a File Is Encrypted?
If a ransomware attack encrypts files audited by FileAudit, the attack will trigger a lot of access events in FileAudit. With mass access alerts, you can immediately detect and get notified of a ransomware attack.
When a file is encrypted, what kinds of file access events can you expect to see? First, the file content needs to be read in order to be loaded in the memory. Then, the data is encrypted in memory, and the encrypted data is written into a new file. Lastly, the original file is deleted.
As a result, FileAudit will show three consecutive file operations:
- A read
- A write
- A delete
So, for FileAudit to detect a massive encryption attack on a file server, you should set three mass alerts:
- One for mass file “Read” events
- One for mass file “Write” events
- One for mass file “Deletion” events
Once set up, if you ever get an alert for all three events at the same time, you know you’re most likely facing a ransomware encryption attack.
Set Up Mass Access Alerts
To set up these alerts, go to the “Alerts Access” Tab, and select “Add a mass alert.”
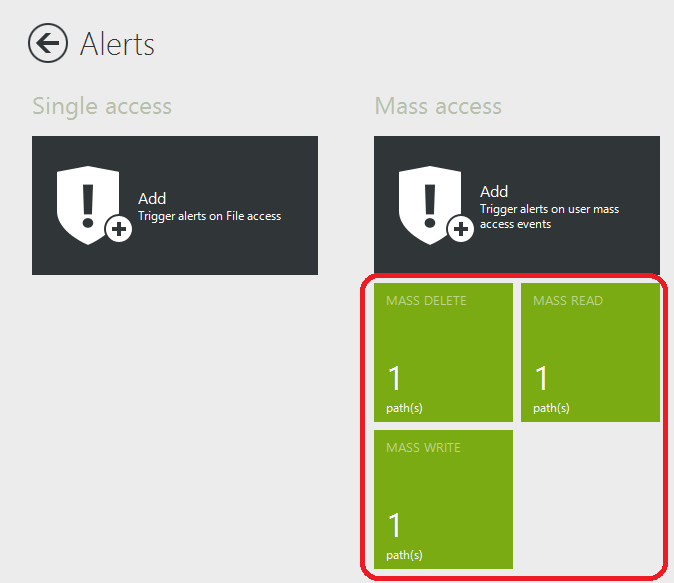
You’ll want to set up three alerts: Mass Read, Mass Delete, and Mass Write.
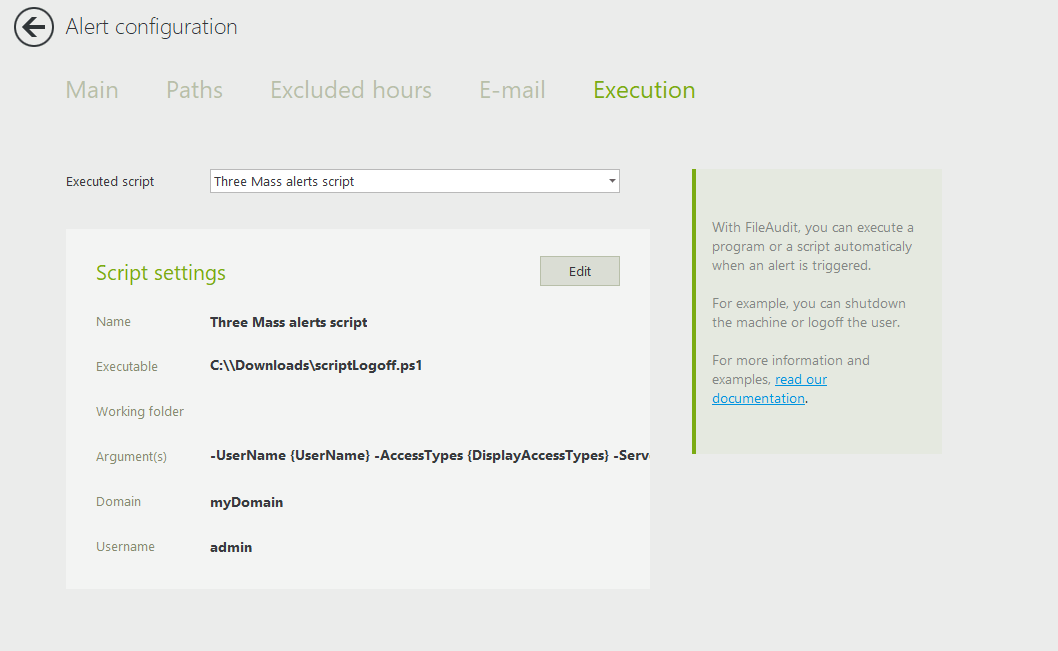
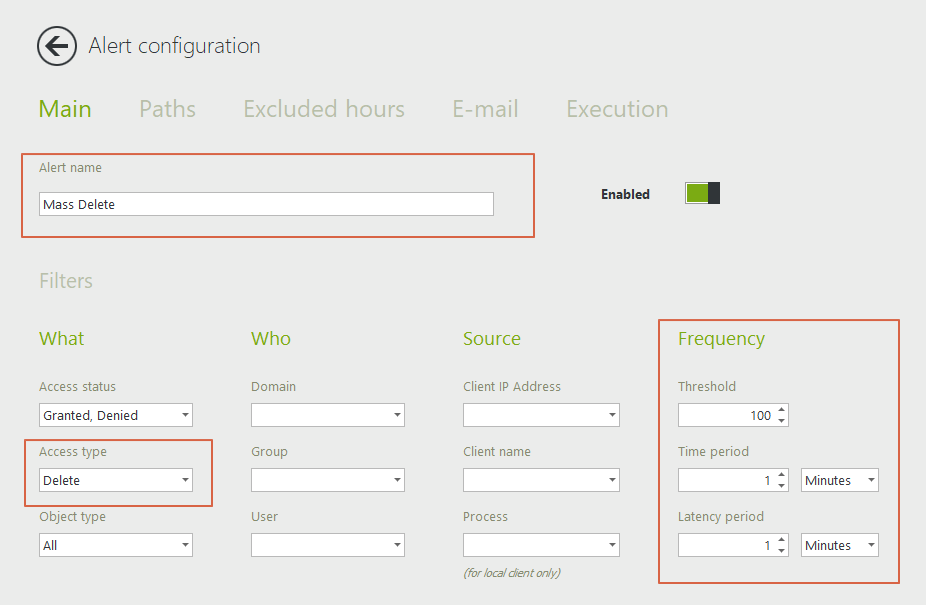
Give each alert a name, and then select the corresponding access type. By default, the threshold is at 100 events in 1 minute. These are our recommended settings. You can modify them if you like, but make sure you configure the same threshold for all three alerts.
Let’s start with a “Mass Delete” alert.
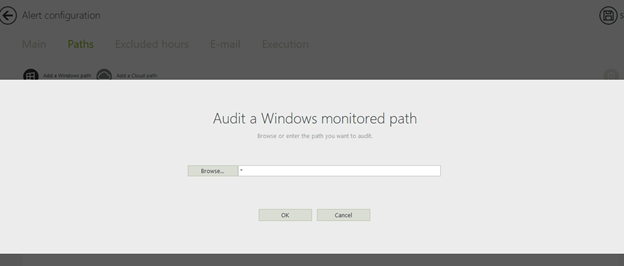
In the paths tab, enter "*":
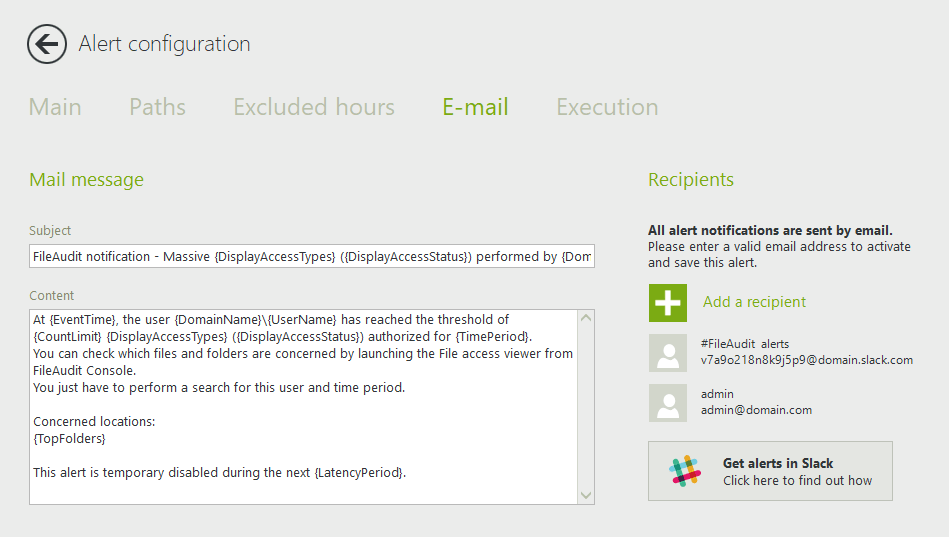
In the email tab, enter the recipients (the people you want to receive the alert):
Save the alert.
Repeat these steps to create your other two alerts for "write" and "read" accesses. Make sure to save the alerts.
You should now see the three alerts in the alerts tab:
Add a Script to React to the Attack in Real Time
Next, you’ll want to add a script. The script will take immediate action to stop the attack when any of these three alerts are triggered – even before an admin gets the notification. In the execution tab, enter a script to logoff the user automatically when the three alerts are triggered.
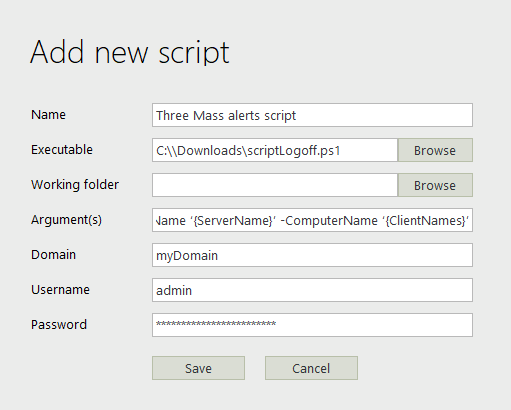
Select from the dropdown menu: Add a new script and enter the details.
To download the script, click here.
Note:
- In details, the argument(s) field is:
-UserName {UserName} -AccessTypes {DisplayAccessTypes} -ServerName ‘{ServerName}’ -ComputerName ‘{ClientNames}’ - The user account that runs the script must be a domain administrator account. This is because the script closes the user session that triggered the alerts (which is the account running the ransomware process).
Save your alert, and add the script to your other two alerts by selecting it from the dropdown menu so that all three have the script configured: